[https://github.com/wand2016/terraformch5example:embed:cite]
ポリシー
main.tf
data "aws_iam_policy_document" "allow_describe_regions" {
statement {
effect = "Allow"
actions = ["ec2:DescribeRegions"]
resources = ["*"]
}
}
resource "aws_iam_policy" "example" {
name = "example"
policy = data.aws_iam_policy_document.allow_describe_regions.json
}- JSONファイルに外出しして
file()関数で読み込んでも同じ
policy.json
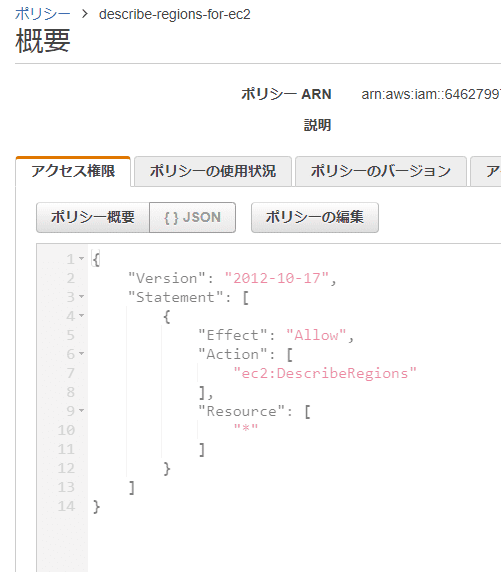
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": ["ec2:DescribeRegions"],
"Resource": ["*"]
}
]
}...
resource "aws_iam_policy" "example" {
name = "example"
policy = file("./policy.json")
}------------------------------------------------------------------------
No changes. Infrastructure is up-to-date.
This means that Terraform did not detect any differences between your
configuration and real physical resources that exist. As a result, no
actions need to be performed.-
HCLの利点
- 変数を使える
- コメントを書くことができる
ロール
信頼ポリシー
- 公式/リソースベースのポリシー
- 「この種類のサービスにのみアタッチできるよ」ってやつ
IAMロール作成、IAMポリシーアタッチ
-
IAMユーザー・ロール・グループにIAMポリシーをアタッチするという世界観
roleはnameで指して、policyはarnで指す…?
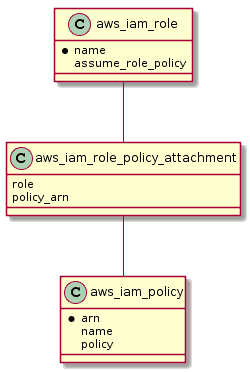
resource "aws_iam_role" "default" {
name = var.name
assume_role_policy = data.aws_iam_policy_document.assume_role.json
}
...
resource "aws_iam_policy" "default" {
name = var.name
policy = var.policy
}
resource "aws_iam_role_policy_attachment" "default" {
role = aws_iam_role.default.name
policy_arn = aws_iam_policy.default.arn
}[https://github.com/wand2016/terraformch5example/blob/master/iam_role/main.tf:embed:cite]
- 名前とポリシーと信頼ポリシーを
varで流し込んで、以降のハンズオンで再利用できるようにする